Is zero trust architecture the future of cyber security?
Author: Mick McLean | Date published: May 4, 2023, UK | Read est: 5 min read
Zero trust isn’t new, but it is still a relatively unknown concept for many enterprises.
As the security landscape continues to get more complex to navigate and protect against, we believe that having a zero trust strategy will be business-as-usual for most enterprises in the not-so-distant future.
In fact, a recent Forrester TEI report found that having a zero trust strategy can reduce the risk of a data breach by 50%, increase the efficiency of security teams by 50%, and accelerate the process to set up end users on new devices by 75%.
So what is zero trust?
It’s a security concept where a user’s access to data and applications is granted on a need-to-know basis, in accordance with a set of predefined rules and always requiring additional verification of the user’s identity.
In contrast to traditional security models in which access is granted based on the trust inherently placed in the network perimeter, zero trust networks require authentication for all access. It will continuously monitor and verify the identity of users and devices attempting to access resources.
In a nutshell, trust is never implied. So users working on the network are treated the same as any users off network.
But is Zero trust an architecture, a framework, or a pipe dream?
We prefer to think of it as a journey.
Designed to protect against threats that originate from inside the network, as well as those that originate outside of it, zero trust architecture is becoming increasingly important in the modern world.
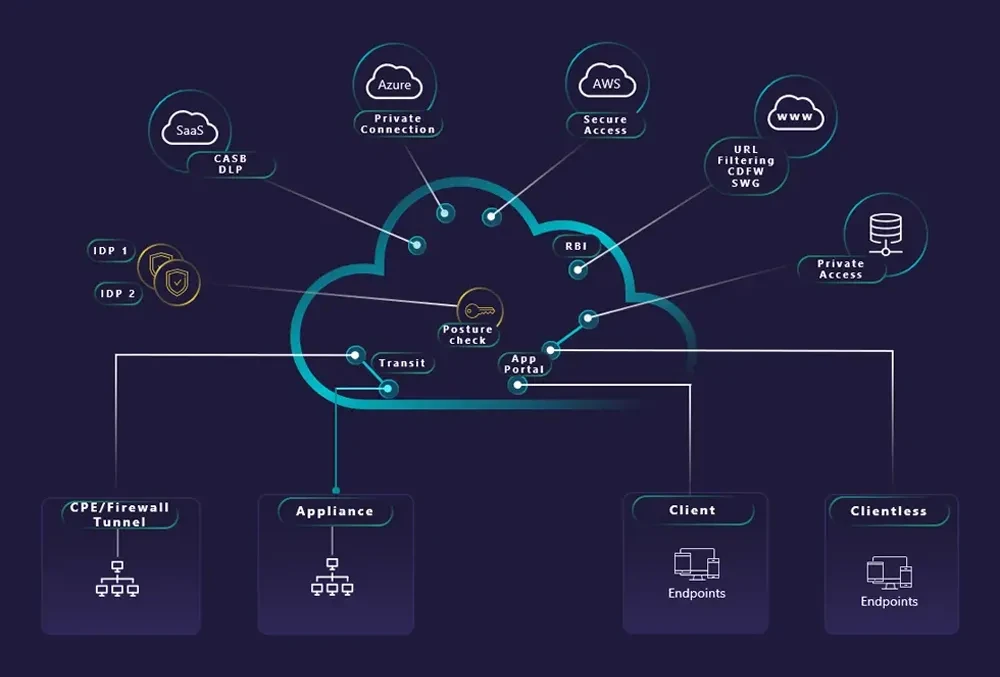
Cyber-attacks are no longer limited to the perimeter of an organisation, with vulnerabilities being exploited in the cloud, mobile devices and IoT, making it increasingly difficult to protect data assets. The threat has grown so much that President Biden signed an executive order mandating zero trust for US government infrastructure.
By implementing a zero trust architecture, organisations can reduce the risk of a data breach, protect their data assets and ensure the security of their users.
The key elements of zero trust
What makes a zero trust architecture? There are three core components:
- Identity and Access Management (IAM)
- Contextual authentication, from user to application
- Application level segmentation (that covers all data, apps, assets and users)
Everything starts with an identity – be that a person, a device, a “thing” or combination of all. Contextual identity adds to the “who” of the entity with the “where” (they are/work), “why” (they are accessing data/ application) and crucially, the “how” (they can access those data/ applications). When an identity attempts to access a resource, it needs to be verified with strong authentication, underpinned by these critical principles:
- Least privilege access
- Behavioural monitoring
- An untrusted network
- Monitoring and visibility
- Verification and inspection (near or real time)
A zero trust policy gives all user groups the least privilege access required for their role, so that other assets are sufficiently segmented and protected. Data protection begins with the ability to identify, classify and label sensitive data so the appropriate policies can be applied to it. Automating such labour-intensive processes is critical.
As well as these policies and governance, other technologies you will see deployed include:
- Data Loss Prevention (DLP)
- Cloud Access Security Broker (CASB)
- Multifactor Authentication (MFA)
- Network/micro segmentation
This may seem like a lot to cover, but zero trust isn’t a one-and-done deployment and doesn’t require ripping out and replacing existing security infrastructure. Rather, it is a series of initiatives and ongoing optimisations that collectively reduce the risk across the business.
Where SASE meets zero trust
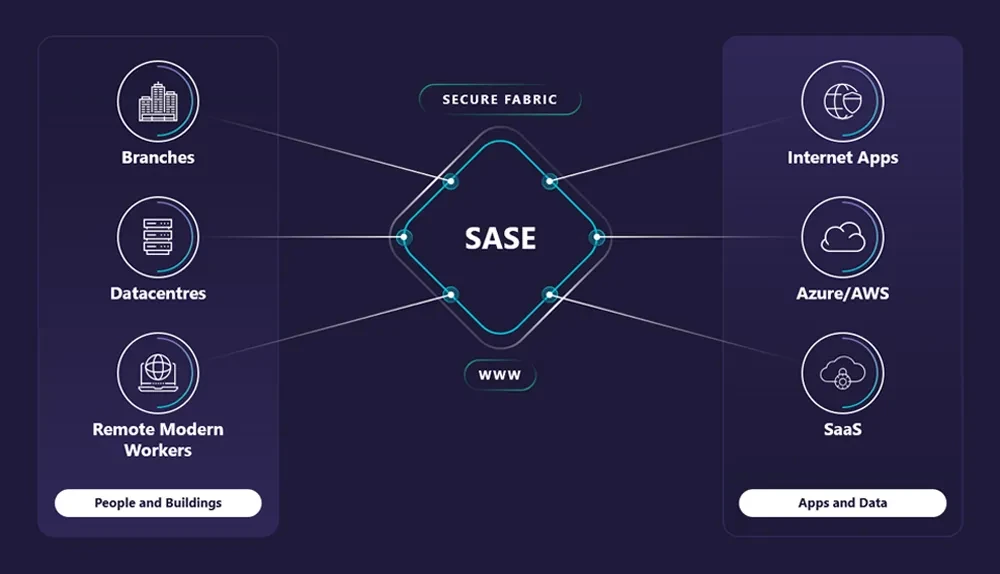
Secure Access Service Edge (SASE) provides a suite of network and security services to securely connect your users to your applications and data. Many of these technologies can be used to help implement a zero trust architecture, but on their own, or simply turned on, don’t provide zero trust.
Zero trust is an element of a wider SASE strategy – it restricts access through all edges (sites, mobile users, and cloud resources) in accordance with zero trust principles. In other words, SASE restricts access through Next-Generation Firewalls (NGFW) and Secure Web Gateway (SWG) capabilities, and zero trust is the degree to which those edges have been restricted.
Alongside its security benefits, SASE bundles Zero Trust Network Access (ZTNA), NGFW and other security services along with network services, such as SD-WAN, WAN optimisation, and bandwidth aggregation, into a cloud-native platform. This means that enterprises that leverage a SASE architecture receive the benefits of zero trust, plus a full suite of network and security solutions that is both simple to manage and highly scalable.
Initial considerations for a zero trust strategy
Zero trust can be further adopted over time and can be done so in line with other strategies (like SASE). Deciding what zero trust looks like for your organisation, especially initially, should be based on your specific risks, current operating model, budget, etc. According to a 2021 report from Microsoft, fewer than 15% of enterprise organisations started implementing zero trust in the same security risk area.
Identifying the risks and minimising the exposure made from hybrid working and remote access to applications are a good starting point to help understand your environment first. You should consider important elements such as, where your documents are actually stored, the importance of applications to business continuity, business processes, and don’t forget good security practices.
Following a framework such as the National Cyber Security Centre (NCSC) helps with good practice, such as vulnerability management, configuration, and governance. It will also help you prioritise the right risks and remediate entire attack chains with a fully integrated toolset and strategic guidance.
Before creating a zero trust architecture, organisations need to consider the following:
- What data assets are most important to protect?
- What risks can be mitigated by implementing a zero trust architecture?
- What type of users/accounts will be accessing the assets?
- What is the lowest level of privileged access that can be granted?
- What type of behavioural monitoring will be required?
- How will your organisation protect its applications and data when access is from outside the network?
- How will your organisation ensure visibility and monitoring of security events?
Take steps today to ensure the security of your organisation’s critical data. Register for our zero trust webinar series, hosted with experts from Focus Group, Cloudflare, Z-Scaler and Infosec, to hear make zero trust achievable for your business.
Or talk to one of our experts today by calling 0800 024 2500, or filling in this form.

Mick McLean
Head of Enterprise Solutions
Focus Group welcomed Mick in 2022. Playing a fundamental role of our Enterprise team, Mick is laser-focused on delivering an outstanding customer experience, through every interaction with Focus Group. Mick ensures we maintain our position as a trusted and expert digital transformation partner.